One of you responded to my
No ROI? No Problem post with this question:
Just read your ROI blog, which I found very interesting. ROI is something I've always tried to put my finger on, and you present an interesting approach. Question: Is it not possible to 'make' money with security, or does it still come down to savings? Example:
- A hospital implements a security system that allows doctors to access patient data from anywhere. Now, instead of doing 10 patients a day they can do (and charge) 13 patients a day.
I'm not trying to sharp shoot you in anyway, I'm just trying to better understand the economics. This is an excellent question. This is exactly the same concept as I stated in my August 2006 post
Real Technology ROI. In this case, doctors are
more productive at accessing patient data by virtue of a remote access technology. This is like installing radios for faster dispatch in taxis. In both cases
security is not causing a productivity gain but security can be reasonably expected as a
property of a properly designed technology. In other words, it's the remote access technology that provides a productivity gain, and doctors should expect that remote access to be "secure." In a taxi, the radio technology provides a productivity gain, and drivers should expect that system to be "secure."
I'm sure that's not enough to convince some of you out there. My point is you must
identify the activity that increases productivity -- and security will not be it. Don't believe me? Imagine the remote access technology is a marvel of security. It has strong encryption, authorization, authentication, accountability, endpoint control, whatever you could possibly imagine to preserve the CIA triad. Now consider what happens if, for some reason, doctors are
less productive using this system. How could that happen? The system is secure! Maybe the doctors all decide to spend tons more time looking at patient records so their "throughput" declines. Who knows -- the point is that
security had nothing to do with this result; it's the business activity that increases (or in this example, decreases) that determines ROI.
What does this mean for security projects? They still don't have ROI.
However, and this is a source of trouble and opportunities, security projects can be components of
productivity enhancing projects that
do increase ROI. This is why the Chief Technology Officer (CTO) can actually devise ROI for his/her projects. As a security person, you would probably have more success in budget meetings if you can tie your initiatives to ROI-producing CTO projects.
Wait a minute, some of you are saying. How about this example: if a consumer can choose between two products (one that is "secure" and one that is not), won't choosing the "secure" model mean that security has a ROI, because the company selling the secure version might beat the competition? In this case, remember that the consumer is
not buying security; the consumer is buying whatever a product that performs some desired function, and security is an "enabler" (to use a popular term). If the two products are functionally equivalent and the same price, buying the "secure" version is a no-brainer because, even if the risk is exceptionally small, "protecting" against that risk is cost free. If the "secure" version is more expensive, now the consumer has to remember his/her CISSP stuff, like Annualized Rate of Occurrence (ARO) and Single Loss Expectancy (SLE) to devise an Annual Loss Expectancy (ALE), where
ARO * SLE = ALE
You then compare your ALE to the cost differential and decide if it's worth paying the extra amount for the "secure" product.
For those of you who still resist me, it's as simple as this: security is almost always concerned with
stopping bad events. When you stop a bad event, you avoid a loss. Loss avoidance means savings, but
no business can stay in business purely by saving money. If you don't understand that you will never be able to understand anything else about this subject. You should also not run a business.
The reason why you
should pursue projects that save money is that those projects
free resources to be diverted to projects with real ROI. Those of you who have studied some economics may see I am getting close to Frédéric Bastiat's
Broken Window fallacy, briefly described by
Russell Roberts thus:
Bastiat used the example of the a broken window. Repairing the window stimulates the glazier’s pocketbook. But unseen is the loss of whatever would have been done with the money instead of replacing the window. Perhaps the one who lost the window would have bought a pair of shoes. Or invested it in a new business. Or merely enjoyed the peace of mind that comes from having cash on hand.Spending money on security breaches is repairing a broken window. Spending money to prevent security breaches is like hiring a guard to try to prevent a broken window. In either case, it would have been more productive to be able to invest either amount of money, and a wise investment would have had a positive ROI. This is why we do not spend time breaking and repairing windows for a living in rich economies.
However, like all my posts on this subject, I am not trying to argue against security. I am a security person, obviously. Rather, I am arguing against those who warp security to fit their own agenda or the distorted worldview of their management.
For an alternative way to talk to management about security, I recommend returning to my post
Risk-Based Security is the Emperor's New Clothes where I cite Donn Parker.









 July's been a great month for controversy on this blog, so I thought I would continue that them by posting word of my
July's been a great month for controversy on this blog, so I thought I would continue that them by posting word of my 
 I'm looking forward to reading
I'm looking forward to reading  I'd like to briefly mention a new book that's great, but which I won't read and review:
I'd like to briefly mention a new book that's great, but which I won't read and review: 
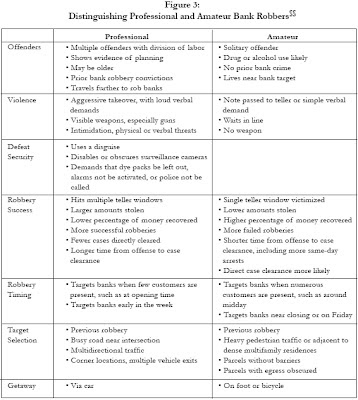
 My seventh
My seventh 
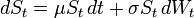




 I also received another book in the mail today,
I also received another book in the mail today,  In the mail today I received a copy of
In the mail today I received a copy of 
 I'm looking forward to reading
I'm looking forward to reading  If you're wondering what my favorite subtitle is, it appears in the nearly ten-year-old book
If you're wondering what my favorite subtitle is, it appears in the nearly ten-year-old book  I am happy to report that work on OpenPacket.org is back on track, thanks to a new volunteer Web application developer.
I am happy to report that work on OpenPacket.org is back on track, thanks to a new volunteer Web application developer.






