Kamis, 31 Januari 2013
make the fake page for any websate you want
share your internet connection and tur your PC to wireless router
Rabu, 30 Januari 2013
Airtel 3G TCP VPN Trick For Feb 2013
As this trick is based on TCP Ports there is always issue of SIM blocking. To avoid SIM blocking disconnect after every use of 275-290 mb. LKet see some features of airtel TCP VPN Trick.
Features Of Airtel TCP VPN Trick
- Works with zero problem.
- Works with default APN : airtelgprs.com
- No registration required.
- HTTPS protocols supported
- Resume supported Downloading.
- Speed capping isuue.
- SIM Blocking [disconnect after every use of 275 mb].
Steps To Setup Airtel TCP VPN Trick
- First download NMD VPN.
- Now download airtel TCP Config file from below link.
- Download Airtel TCP VPN Book Config.
- Now extract downloaded Config files and paste it in NMD VPN Config folder.
- Run NMD VPN as Administrator and connect with given Config.
- Connection will be established instantly.
- Enjoy free 3G!! :)
Screenshot Of Airtel TCP VPN Trick
move the mouse cursor with your head
try it
to get the program
eviacam.sourceforge.net/
Selasa, 29 Januari 2013
Senin, 28 Januari 2013
Vodafone 3G TCP VPN Trick For Feb 2013
Features Of Vodafone TCP VPN Trick
- Based on high speed servers
- Https protocols are supported
- Average speed
- Resume Supported Downloading
- Torrent downloading supported
- No registration required
Steps To Configure Vodafone TCP VPN Trick
- First download Vodafone TCP Config file from below link
- Download Vodafone TCP Config
- After downloading extract the config files and paste it into NMD VPN Folder.
- Download NMD VPN (if you don't have)
- Now connect with APN as www
- Now run NMD VPN as Administrator and connect with Vodafone TCP Server.
- It will be connected immediately.
- Enjoy using free Voadfone 3G!!!!
Screenshot Of Vodafone 3G Trick
Sabtu, 26 Januari 2013
On Thought Leadership and Non-Technical Relevance
 A reader left a comment on my post 2012: The Year I Changed What I Read. He said:
A reader left a comment on my post 2012: The Year I Changed What I Read. He said: Richard, it's interesting to note that your career has shifted from "pure" technology to more of a thought leadership role where you can leverage your training and interest in history, political science, etc. I wonder if you ever expected to become such a public figure in the whole debate about China when you first started with infosec?
Your career path is an encouraging example for others to follow. Even though I work in technology, I also have a sociology/political science background and I've been wondering how I can leverage those interests, especially as I get older and cheaper/hungrier techies continue to enter the industry.
Thank you for your comment and question. I will try to answer here.
I did not plan to become a "public" figure, and I don't necessarily consider myself exceptionally "public" now. I just reviewed my TaoSecurity news page to see when I first started speaking at conferences. Before joining Foundstone, I spoke at a few events because I believed too few people were discussing incident detection and traffic analysis. Once I joined Foundstone in April 2002 as a member of Kevin Mandia's incident response team, I became a public speaker out of necessity. Kevin and Foundstone expected consultants to speak, teach, and write, in addition to performing consulting duties. I've stayed in that mindset ever since, although I speak, teach, and write on increasingly diverse topics.
I see the "thought leadership" question in two ways. First, I took deliberate actions to get my thoughts to the world. I wrote my books and post to this blog as a way to capture my thinking on a coherent set of subjects. I hope they are useful to others, but I see these as outlets for self-expression.
The second way I think about "thought leadership" involves my work duties. If you look at my press page you will see a jump in activity in 2011, the year I joined Mandiant. In addition to being CSO, I'm also responsible for speaking with the press, industry analysts, policy makers, and some customers and prospects. I enjoy these opportunities because I realize there are a lot of sources for tools but few for methodologies and operational processes. To the extent I can share my recommendations for how to combat intruders and avoid wasting resources or pursuing dead ends, I consider this second form of thought leadership a success.
Finally, let me address the point about leveraging what are traditionally "non-security" skills or interests, namely history and political science. As I've posted and Tweeted earlier, the world is waking up to the fact that the techies and engineers don't have all the answers. Every time you hear someone say that the answer is to build Internet 2, and "get it right," you're listening to an "engineering first" mindset.
I love engineers (my dad is one, I took plenty of engineering in college, I work with engineers, etc.) but their viewpoint is but one of many. Technical knowledge doesn't give anyone a golden ticket to good policy. If we don't engage people who understand lessons of history and policy, we'll continue to lose when facing advanced intruders.
I would argue that a person who knows technology, security, history, and politics is equipped to be very valuable to an organization trying to build a mature security operation, or that seeks to influence policy. Your interests and skills may not align with your current role, so you may need to keep those strengths in mind when looking for a job better aligned with history and politics.
I think the key is to strive to stay relevant in whatever area interests you. If you like non-technical subjects, you've got to stay current with them and develop your thoughts and analysis on those issues the same as you might with technical topics.
Thank you for your comment. I welcome other comments here or on Twitter.
Jumat, 25 Januari 2013
Tip of the Day - A smarter way to eat microwave popcorn
 |
| Don't know why it took me 20+ years to figure out how to eat popcorn this way. |
Super pro tip: flip the popcorn over and cut off the bottom side. This side is usually greasier. If you cut this off, usually it will bring up some left over kernels stuck to the bag; also the top side (now bottom side) is a lot less greasy so you can feel ok about putting it on a table or lap or whatever.
Cloud Storage 2013 - A look at the old and the new
By now, everyone uses cloud storage. Whether you knowingly download a program (Dropbox) to sync certain files you deem important, or unknowingly have and use files that are in the cloud (Google Drive), cloud storage is a part of our everyday life. In a quest to find cloud storage the suits my specific needs, I am compiling a list of the advantages and disadvantages to various cloud storage as seen in the beginning of 2013.
Before I begin, I should reveal my biases. Cloud storage for me, should meet the following demands:
- Have some sort of desktop client that automates syncing.
- Cross platform compatible. For me Linux and Android clients are essential.
- Have a free storage amount that is actually useful.
- Ability to share files with others.
Senin, 21 Januari 2013
Minggu, 20 Januari 2013
Latest Idea UDP VPN Trick Working In Many States
Lets see some features of this Idea UDP VPN Trick and Sheild VPN.
Features Of Idea UDP VPN Trick
- No need to register for any Account
- Based on UDP Ports
- High Speed Data Transfer
- HTTPS Protocols are supported
- No disconnection issue
- Torrent and other client supported.
- Resume Supported Downloading
Steps To Configure Idea UDP VPN Trick
- First Download Shield VPN configured for Idea
- Connect your with APN as mobile
- Now Run Shield VPN.
- Select Expact Shield server from choose server option
- Leave username and password field blank
- Now Select protocol as UDP and port as 9200
- Now click on connect Button
- It will connect instantly
- Enjoy free 3G!!!
Screenshot Of Idea UDP VPN Trick
Kamis, 17 Januari 2013
Airtel TCP VPN Trick Working In Many States - Jan 2013
Features Of Airtel TCP VPN Trick
- Based on premium servers.
- Works with default APN : airtelgprs.com
- No registration required.
- Based on the TCP Ports.
- Resume supported Downloading.
- Speed capping isuue.
- No SIM Blocking.
Steps To Configure Airtel TCP VPN Trick
- First Download Airtel TCP VPN Config files from here
- Copy the Download Config in NMD VPN config folder
- Download NMD VPN if you don't have
- Now connect with APN as airtelgprs.com
- Now Run NMD VPN as Administrator and connect with Airtel TCP config.
- It will connect instantly
- Enjoy!!!
Screenshot Of Airtel 3G TCP VPN Trick
Visit daily for More Airtel tricks, also like us on facebook and stay updated with latest tricks. If you face any problem with this trick then do comment below you will get reply as soon as time allows!
Rabu, 16 Januari 2013
How to Win This TCP/IP Book
Thanks to No Starch Press I have a brand-new, shrink-wrapped copy of The TCP/IP Guide, a mammoth 1616 page hardcover book by Charles M. Kozierok.
Here's what you have to do to try to win this book: submit a case study on how network security monitoring helped you detect, respond to, and contain an intrusion in your environment.
You don't have to reveal your organization, but I want to know some general information like the number of users and computers. Readers need to know the sort of environment where NSM worked for you, but I don't want you to reveal your organization (unless you want to).
Tell the reader what happened, what NSM data you used, how you used it, and how you handled the incident. Extra points go to writers who include log excerpts and screen captures.
I will include the submission in my new book, subject to editing by myself and No Starch, for readability and comprehension.
The deadline for submission is 10:00 pm eastern time, Saturday 26 January (sorry for the earlier typo). I managed to extend the deadline a little. Quality trumps quantity here -- I'm not looking for another chapter!
Please submit your entries as plain text in email to taosecurity at gmail dot com. I won't open .doc or .pdf or other files which could contain surprises.
When you take screen captures, save them in high-resolution .tif format without compression. Don't take a capture of command-line information; instead, copy the text into the story. When taking screen captures of GUI tools and the like, don't take a capture of a giant window; resize to something that will be legible on a printed page, witha .
This is an example of a bad screen capture:
This is a good screen capture:
Depending on the quality of any screen captures, I may ask you to resubmit them to meet the publisher's requirements.
If you have any questions, please post them here.
The winner will receive the pictured TCP/IP book. Once my new book arrives, I will ask the publisher to mail you a free copy too.
If I receive one or more good runners-up, I will ask the publisher to send their owners copies of my new book too.
If you have any questions, please submit them as comments here. Good luck!
Selasa, 15 Januari 2013
Airtel UDP 53 VPN Trick Working Again For 2013
This trick is working without any speed capping issue. Just download the given config and start using free highspeed 3G. Lets see some features of this UDP Trick.
Features Of Airtel UDP 53 VPN Trick
- No Speed Capping issue.
- Highspeed parallel downloading.
- Based on the UDP Port 53.
- Based on default APN : airtelgprs.com
- No disconnection Problem.
- Can also be used with PD Proxy.
- No need to register for any account.
Steps To Configure Airtel UDP VPN Tricks
- Download Config file from here
- Download NMD VPN [if you don't have it]
- Extract the downloaded config files and pate it in NMD VPN config folder
- Now connect to internet using APN airtelgprs.com
- Run NMD VPN as Administrator and connect with given config.
- It will connect instantly without any issue.
- Enjoy!!!!
Screenshot of Airtel 3G UDP Trick
Minggu, 13 Januari 2013
Bitshare Premium Link Generator - 2013
To start downloading with premium link you must have IDM or any other download manager to be installed on your PC. Download will start in IDM instanly when you click on download.
Kindly share this post with your friends if it helped you. Also like us on facebook and subscribe for email updates. If you face any problem regarding Bitshare Premium link generator do comment below.
Jumat, 11 Januari 2013
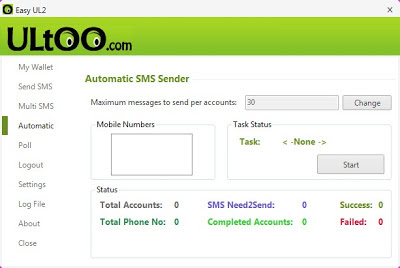
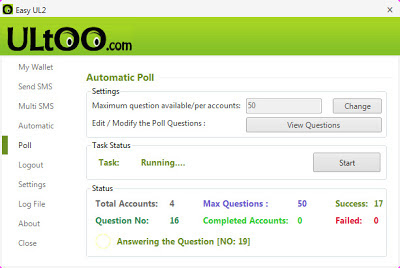
Ultoo Multisender Desktop Client V1.3 - 2013
There is no special configuration required to use this ultoo desktop client. Just follow below mentioned steps carefully and you easily earn from ultoo using this app. First download the app from below link
Steps To Use Ultoo Desktop Client 2013
- After downloading Ultoo destop client extract.
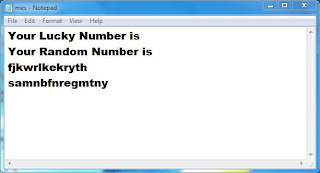
- Now edit the file acc.txt and enter account and password in below manner
- your account number give a single space and type password and save it.[see below image]
- Now edit the file mes.txt and enter your random messages in each line.[see below image]
- Now edit the file pum.txt and enter your random number in each line.[see below image]
- Now open the file Easy UL2.exe and login with your username and password and start earning
Kamis, 10 Januari 2013
Airtel Back Query Trick For Jan 2013
Features Of Airtel 3G Back Query Trick
- No Speed Capping Problem
- Can be used in default browser
- Can be used with official UC Handler
- No need to setup any VPN
- HTTPS protocols are supported
- No need register for any external Account
- Resume Supported downloading.
- Uploading Supported
Steps To Configure Airtel Back Query Trick
- Account name: Thefuturehack
- Access Point: airtelgprs.com
- Proxy: 93.174.123.22
- Port: 80
- Home Page: google.com
- Now open Opera Mini or UC Handler and enter any back query from below mentioned
- Download UC Handler
- ?fb.nimbuzz.com/upload
- ?AirtelFB.nimbuzz.com/upload
- ?m.nimbuzz.com/upload
- ?203.115.112.29.nimbuzz.com/upload
- ?203.115.112.5.nimbuzz.com/upload
Selasa, 08 Januari 2013
Latest Airtel Front Query Trick - Jan 2013
Features Of Airtel 3G Front Query Trick
- No Speed Capping Problem
- Can be used in default browser
- Also works with UC Handler
- No need to setup any VPN
- Based on highspeed proxies
- HTTP protocols are supported
- No need register for any external Account
- No Resume Supported downloading.
Steps To Use Airtel Front Query Trick In Mobile
- Account name: Thefuturehack
- Access Point: airtelgprs.com
- Proxy: 93.174.123.22
- Port: 80
- Home Page: Leave it blank or type google.com
- Now open Opera Mini Handler and enter below front query
- free ip/cgi-bin/nph-proxy.cgi/000001A/http/
Steps To Use Airtel Front Query Trick In PC
- Profile Name: Thefuturehack_Airtel
- Select Static APN and Enter Access Point as: airtelgprs.com
- Now open your browser Firefox or Chrome. read more
- In Network Settings Enter below mentioned proxy and port
- Proxy: 93.174.123.2213
- Port: 80
- Set Home Page as: free ip/cgi-bin/nph-proxy.cgi/000001A/http/
- Now save the setting and open your homepage.
For Resume Supported Downloading
- Proxy : 50.22.79.99
- Port: 80
- FrontQuery : free ip/~anonycgi/nph-andripzf.cgi/20/http/
Kindly share this post with your friends if it helped you. Also like us on facebook and subscribe for email updates. If you face any problem regarding this trick do comment below.
Bejtlich's New Book: Planned for Summer Publication
 Nearly ten years after I started writing my first book, the Tao of Network Security Monitoring, I'm pleased to announce that I just signed a contract to write a new book for No Starch titled Network Security Monitoring in Minutes.
Nearly ten years after I started writing my first book, the Tao of Network Security Monitoring, I'm pleased to announce that I just signed a contract to write a new book for No Starch titled Network Security Monitoring in Minutes. From the book proposal:
Network Security Monitoring in Minutes provides the tactics, techniques, and procedures for maximum enterprise defense in a minimum amount of time.
Network Security Monitoring (NSM) is the collection, analysis, and escalation of indications and warnings to detect and respond to intrusions. Network Security Monitoring in Minutes teaches information technology and security staff how to leverage powerful NSM tools and concepts immediately.
Using open source software and vendor-neutral methods, the author applies lessons he first began applying to military networks in 1998. After reading this book, the audience will be able to integrate the same winning approaches to better defend his or her company’s data and networks.
Network Security Monitoring in Minutes is an important book because nearly all organizations operate a network. By connecting to the Internet, they expose their intellectual property, trade secrets, critical business processes, personally identifiable information (PII), and other sensitive information to attackers worldwide. Without the network level vigilance provided by this book, organizations will continue to be victimized for months, and in many cases years, before learning they have been breached.
This book consists of the following chapters:
Chapter 1, Network Security Monitoring Rationale, explains why NSM matters and help readers gain the support needed to deploy NSM in their environment.
Chapter 2, Accessing Network Traffic, addresses the challenges and solutions surrounding physical access to network traffic.
Chapter 3, Sensor Deployment and Configuration, introduces Security Onion (SO), and explains how readers can install the software on spare hardware to gain an initial NSM capability at low or no cost.
Chapter 4, Tool Overview, guides the reader through the core SO tool set, focusing on those capabilities most likely to help handle digital intrusions.
Chapter 5, Network Security Monitoring Operations, shares the author’s experience building and leading a global Computer Incident Response Team (CIRT), such that readers can apply those lessons to their own operations.
Chapter 6, Server-Side Compromise, is the first NSM case study, wherein readers will learn how to apply NSM principles to identify and validate a compromise of an Internet-facing application.
Chapter 7, Client-Side Compromise, is the second NSM case study, offering readers an example of a user being victimized by a client-side attack. NSM data will again identify and validate the compromise, prompting efficient incident response.
The Conclusion extends NSM principles beyond the enterprise into hosted and Cloud settings, offering future options for those environments.
The Appendix discusses tools that are not open source, but which may be helpful to those conducting NSM operations.
My goal is to finish this short book (roughly 220 pages) in time for publication at Black Hat this summer. Thank you to Pearson/Addison-Wesley for giving me the flexibility to write this complementary NSM book, and to No Starch for signing me to their publishing house.
Happy 10th Birthday TaoSecurity Blog
I wrote my first post on 8 January 2003 while working as an incident response consultant for Foundstone wortking for Kevin Mandia. Today I am Chief Security Officer at Mandiant, back working for Kevin Mandia. (It's a small world.)
With 2905 posts published over these 10 years, I am still blogging -- but much less. Looking at all 10 years of blogging, I averaged 290 per year, but in the age of Twitter (2009-2012) I averaged only 144 blog posts per year. Last year I wrote 60 times.
Why the drop over the years? First, I "blame" my @taosecurity Twitter account. With over 15,000 followers, easy posting from mobile devices, and greater interactivity, Twitter is an addictive platform. However, I really enjoy Twitter and make the trade-off gladly. It would be nice to become a verified user though, with access to two-factor or two-step authentication.
Second, blogging used to be the primary way I could share my ideas with the community. These days, speaking and writing are a big part of my professional duties. For example, last year news outlets quoted me 55 times. Those citations represent hundreds of hours spent talking to the press, explaining how security works and how to improve our situation. I also wrote for the Mandiant Blog, and spoke or taught at 22 events. At the end of many days, I feel like I'm getting my message out without blogging.
Third, time is precious. I enjoy spending time with my family, or reading, or working out, or learning to play guitar when I'm not working for Mandiant.
However, I still plan to keep blogging in 2013. Twitter's only a 140 character platform, and some days I have the time and inclination to share a few thoughts beyond what I've said or written for work.
To celebrate the blog's 10th birthday, I will be announcing a book giveaway on my @taosecurity Twitter account either today or before the end of the week. Follow me on Twitter for details.
Before finishing I'd like to thank Blogger, now part of Google, for providing me this free platform for the past ten years. Way to go!
In my next post I will share word on an exciting new project. Stay tuned.
Senin, 07 Januari 2013
Welcome to Network Security Monitoring in the Cloud
I just watched an incredible technical video. If you have about 10 minutes to spare, and want to be amazed, take a look at Snorby Cloud.
I think the video and Web site does an excellent job explaining this new offering, but let me provide a little background.
Many of the readers of this blog are security pros. You're out there trying to defend your organization, not necessarily design, build, and run infrastructure. You still need tools and workflows that accelerate your incident detection and response process though. So, you work as a security admin, system admin, storage admin, database admin... you get the picture. You manage to keep up, but you probably wish you could focus on finding bad guys, as quickly as possible, without taking care of all the *stuff* that you need to do your job.
While many of you are security experts, some are just beginning your journeys. The responsibilities of being an admin of four or more different shades is overwhelming. Furthermore, you don't have the experience, or budget, or support to get the security data and escalation paths needed to defend your network. How can you improve your skills when you're constantly overwhelmed?
Both kinds of users -- senior and junior alike -- are going to find something intriguing about Snorby Cloud. Maybe you've heard of Snorby before, as a Web-based interface to Network Security Monitoring data. Doug Burks packages it with Security Onion (SO), and you can try it via live CD or .iso in a VM. It looks great on my iPad! There's even a mobile version on iTunes.
Snorby Cloud would be cool if it just put the Snorby Web application in the cloud, and managed the administrative side of security infrastructure for you. For example, you'd log into the cloud interface and be greeted by the graphs you remember from traditional Snorby.
However, you have to think of this as a new, better version of Snorby, collecting far more useful data, and making it rapidly available to the analyst. For example, the following shows SMTP logs available in the interface:
You can just as easily access host-based logs for the same victim computer:
As you investigate the incident, you can see who else on your team is working and what they did. You can also chat with them in real time.
I could say a lot more about this new tool, but I think watching the video will convey some of what it can do. My next step is to get the agents running on a test network so I can drive the console myself and become more familiar with it.
Snorby Cloud is a product from Packet Stash. Follow them at @packetstash for updates.
Disclaimer: I'm friends with this team; I hired two of the co-founders into GE-CIRT, and later worked with all three co-founders at Mandiant.
Minggu, 06 Januari 2013
Airtel PD Proxy Trick Working Again - Jan 2013
Features Of Airtel 3G PD Proxy Trick
- Based on Trial Account
- Can be used at any balance
- Minimum 3G recharge required to get 3G Speed
- HTTPS protocols are supported
- Resume Supported downloading in IDM.
Steps To Configure Airtel PD Proxy Trick
- First Register your account on PD Proxy using this link
- Download PD Proxy from here
- Note down your username and password
- Go to setting Tab Click on advance setting
- Go to Proto Options >> TCP Server Port >> Port:443
- Now click Parent Proxy >> Enable Parent Proxy and enter below IP and Port
- IP: 80.239.243.210
- Port: 80
- Go to Parent Proxy >> Headers and enter any header from below or any working HP
- Headers : Host:10.11.233.29 X-Online-Host:10.11.233.29
- Headers : Host:fb.me/wapbrowsing.php/00/http/
Screenshot Of Airtel PD Proxy Trick
Kindly share this post with your friends if it helped you. Also like us on facebook and subscribe for email updates. If you face any problem regarding this trick do comment below.
Sabtu, 05 Januari 2013
Vodafone 3G Proxy Trick Working - Jan 2013
Features Of Vodafone 3G Proxy Trick
- No Speed Capping Problem
- Based on default Apn www
- No need register for any external Account
- Based on highspeed proxies
- Minimum balance RS 1 required.
- HTTPS protocols are supported
- Resume Supported downloading in IDM.
Steps To Use Vodafone 3G Proxy Trick In Mobile
- Account name: Thefuturehack_Vodafone
- Access Point: www
- Proxy: 72.10.53.126
- Port: 80
- Home Page: http://203.115.112.27 or any working in your State
- Now save the setting and open your homepage.
Steps To Use Vodafone 3G Proxy Trick In PC
- Profile Name: Thefuturehack_Vodafone3G
- Select Static APN and Enter Access Point as: www
- Now open your browser Firefox or Chrome. read more
- In Network Settings enter below mentioned proxy and port
- Proxy: 72.10.53.126
- Port: 80
- Set Home Page as: http://203.115.112.27 or any working in your State
- Now save the setting and open your homepage.
- Done! Enjoy free high speed Vodafone 3G!!!
Screenshot For Vodafone 3G Proxy Trick
Kindly share this post with your friends if it helped you. Also like us on facebook and subscribe for email updates. If you face any problem regarding this trick do comment below.
Kamis, 03 Januari 2013
New Airtel TCP VPN Trick - 100% Working
Steps To Use New Airtel TCP VPN Trick
- Download Airtel TCP VPN Config from here
- Copy and paste the config files in NMD VPN Config folder.
- If you don't have NMD VPN download it form here
- Now connect with APN as airtelgprs.com
- Run NMD VPN as Administrator.
- Connect with any given servers.
- It will connect instantly without any issue
- Done! Enjoy Free High Speed Airtel 3G!!!!
Screeshot Of New Airtel TCP VPN Trick
This trick is tested and its confirmed to be working Rajasthan, Delhi, U.P and some other States also. However you can try this trick in your States if TCP ports are opened in your States.
Kindly share this post with your friends if it helped you. Also like us on facebook and subscribe for email updates. If you face any problem regarding this trick do comment below.
Rabu, 02 Januari 2013
Security Onion + (ELSA or Snorby) + CapMe = Awesome
Monday Doug Burks released Security Onion 12.04. Please read Doug's post to learn how great this new 64 bit release is. I wanted to highlight a few features of the new release which takes Network Security Monitoring with open source tools to a new level for security analysts.
12.04 ships with Martin Holste's Enterprise Log and Search Archive (ELSA) working out of the box. Thanks to close integration with the latest version of Bro, analysts have Web-based, indexed access to Bro logs.
If that weren't enough, 12.04 also ships with a late addition -- Paul Halliday's CapMe. What this means is that you can now access full TCP transcripts from any alert in Dustin Webber's Snorby or Martin's ELSA.
You might not appreciate that right away, but it's a step in the right direction. Thus far, Bamm Visscher's Sguil has been the de facto open source NSM reference tool, allowing analysts to easily pivot from alert or session data to full pcap data. Now, with ELSA + CapMe, analysts can pivot from any log entry of TCP traffic with timestamps, IP addresses, protocols, and ports to a Web-based rendering of a transcript.
This is key: this transcript was not saved because of the log or alert. It was saved simply because the traffic was seen on the wire and netsniff-ng recorded it. This is one way to better handle threats who know how to evade signature-based systems.
This new workflow/feature is what I chose to depict in the screen shot at left. The upper window shows ELSA with a query for a BRO_HTTP log for www.testmyids.com. I then invoke CapMe and generate the transcript in the window at bottom. You can do the same from alert data in Snorby.
This is only the first step in giving analysts more data via open source software. Great work Security Onion team!
Selasa, 01 Januari 2013
New Airtel 3G Proxy Trick - Working In Many States
Features Of Airtel 3G Proxy Trick
- No Speed Capping Problem
- No need to setup any VPN
- No Disconnection Problem at all.
- Based on highspeed proxies
- HTTPS protocols are supported
- No need register for any external Account
- Resume Supported downloading.
Steps To Use Airtel 3G Trick In Mobile
- Account name: Thefuturehack
- Access Point: airtelgprs.com
- Proxy: 76.73.71.203 or 63.141.241.213
- Port: 80
- Home Page: http://203.115.112.5 or any working in your State
- Now save the setting and open your homepage
- Done!
Steps To Use Airtel 3G Trick In PC
- Profile Name: Thefuturehack_Airtel
- Select Static APN and Enter Access Point as: airtelgprs.com
- Now open your browser Firefox or Chrome. read more
- In Network Settings enter below mentioned proxy and port
- Proxy: 76.73.71.203 or 63.141.241.213
- Port: 80
- Set Home Page as: http://203.115.112.5 or any working in your State
- Now save the setting and open your homepage.
- Done! Enjoy free high speed 3G!!!















.jpg)