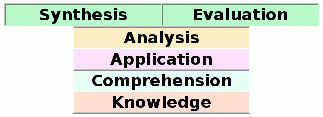
Twenty years ago, when some of my readers were busy being born, I was a high school freshman. My favorite instructor, Don Stavely, taught history. One of the educational devices he used was Bloom et al.'s Taxonomy of the Cognitive Domain, pictured at left. This hierarchy, which travels from bottom to top, is a way to describe a student's level of understanding of a given subject.
These descriptions from Purdue are helpful:
- Knowledge entails the ability to recall or state information.
- Comprehension entails the ability to give meaning to information.
- Application entails the ability to use knowledge or principles in new or real-life situations.
- Analysis entails the ability to break down complex information into simpler parts and to understand the relationships among the parts.
- Synthesis entails the act of creating something that did not exist before by integrating information that had been learned at lower levels of the hierarchy.
- Evaluation entails the ability to make judgments based on previous levels of learning to compare a product of some kind against a designated standard.
I find this to be a useful way to evaluate mastery of a given subject.
For example, I propose many people detest technical certifications because they perceive the candidates as simply working at the knowledge level.
I think many people were disappointed by the removal of the SANS practical requirement, because meeting that challenge required work at the synthesis level -- a very high mark indeed.
I keep this hierarchy in mind when I review books. If I am reading material related to network security monitoring, I can absolutely make judgements not only about accuracy but also about relevance and worth. That's an evaluation level activity. On the other hand, books about reverse engineering malicious code might strain my ability to review at the comprehension or even the knowledge level when discussing assembly language.
If you're responsible for hiring people, you might consider using some of these ideas in your interviews. A security architect should demonstrate skills at the synthesis or evaluation levels, while those on the entry level should function at least at the knowledge level.














0 komentar:
Posting Komentar