Note: image from ike-scan wiki
Ok guys, I know ike-scan is out there for some time, but still i would love to blog about this. Cisco VPNs runs on UDP port 500 and most of us knows that Cisco VPN Concentrator 3000 is vulnerable to multiple attacks like DoS and Buffer Overflow. ike-scan will actually test for the presence of VPNs and check if the VPN is able to be forced into the Aggressive mode for cracking later on. And once the PSK is cracked, connection to the vulnerable server should be no problem. Personally, i had tested multiple VPNs and only find a Cisco VPN Concentrator 3000 vulnerable. Well, if you would love to know how to pen-test VPN, check out the following articles below:
http://www.nta-monitor.com/wiki/index.php/Ike-scan_User_Guidehttp://www.securityfocus.com/infocus/1821It will be very useful if you can go through the whole article and understand how IPSec works. As a penetration tester, below are the few commands i always used in the command prompt:
C:\ikescan>ike-scan xx.xx.xx.xx
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
Ending ike-scan 1.9: 1 hosts scanned in 2.531 seconds (0.40 hosts/sec). 0 retur
ned handshake; 0 returned notify
C:\ikescan>ike-scan -auth=3 xx.xx.xx.xx
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
Ending ike-scan 1.9: 1 hosts scanned in 2.484 seconds (0.40 hosts/sec). 0 retur
ned handshake; 0 returned notify
C:\ikescan>ike-scan -auth=1 xx.xx.xx.xx
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
Ending ike-scan 1.9: 1 hosts scanned in 2.484 seconds (0.40 hosts/sec). 0 retur
ned handshake; 0 returned notify
C:\ikescan>ike-scan -auth=64221 xx.xx.xx.xx
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
Ending ike-scan 1.9: 1 hosts scanned in 2.484 seconds (0.40 hosts/sec). 0 retur
ned handshake; 0 returned notify
C:\ikescan>ike-scan -sport=0 -auth=64221 xx.xx.xx.xx
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
Ending ike-scan 1.9: 1 hosts scanned in 2.484 seconds (0.40 hosts/sec). 0 retur
ned handshake; 0 returned notify
C:\ikescan>ike-scan -multiline -sport=0 --trans=5,2,1,2 --aggressive xx.xx.xx.xx
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
Ending ike-scan 1.9: 1 hosts scanned in 2.468 seconds (0.41 hosts/sec). 0 retur
ned handshake; 0 returned notify
C:\ikescan>ike-scan -multiline -sport=0 --trans=5,2,1,2 --vendor=00 xx.xx.xx.xx
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
Ending ike-scan 1.9: 1 hosts scanned in 2.453 seconds (0.41 hosts/sec). 0 retur
ned handshake; 0 returned notify
C:\ikescan>ike-scan -multiline -sport=0 --trans=5,2,1,2 --vendor=f4ed19e0c114eb5
16faaac0ee37daf2807b4381f xx.xx.xx.xx
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
Ending ike-scan 1.9: 1 hosts scanned in 2.453 seconds (0.41 hosts/sec). 0 retur
ned handshake; 0 returned notify
C:\ikescan>ike-scan -multiline -sport=0 --trans=5,2,1,2 --aggressive xx.xx.xx.xx
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
Ending ike-scan 1.9: 1 hosts scanned in 2.468 seconds (0.41 hosts/sec). 0 retur
ned handshake; 0 returned notify
C:\ikescan>ike-scan -multiline -sport=0 --trans=5,2,1,2 --aggressive xx.xx.xx.xx
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
Ending ike-scan 1.9: 1 hosts scanned in 2.468 seconds (0.41 hosts/sec). 0 retur
ned handshake; 0 returned notify
C:\ikescan>
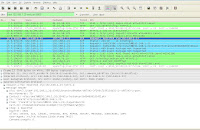
ike-scan -multiline -sport=0 --trans=5,2,1,2 --aggressive xx.xx.xx.xx 443As you can see the list goes on and on. In the last example highlighted in black, i specify the port to check if the VPN is running at port 443. I know Nortel can have VPN gateways running on SSL. The above results are from a Nortel VPN Gateway.
If you successfully found a vulnerable VPN server, the response would be as shown below:
C:\ikescan>ike-scan -v -s 0 xx.xx.xx.xx
Starting ike-scan 1.8 with 1 hosts (http://www.nta-monitor.com/ike-scan/)
xx.xx.xx.xx Main Mode Handshake returned HDR=(CKY-R=fb07f15c64c1fef9) SA=(En
c=DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800) VI
D=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
Ending ike-scan 1.8: 1 hosts scanned in 0.114 seconds (8.77 hosts/sec). 1 retur
ned handshake; 0 returned notify
--------------------------------------------------------------------------------------------------
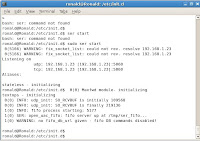
C:\ikeprobe>ikeprobe xx.xx.xx.xx
IKEProbe 0.1beta (c) 2003 Michael Thumann (www.ernw.de)
Portions Copyright (c) 2003 Cipherica Labs (www.cipherica.com)
Read license-cipherica.txt for LibIKE License Information
IKE Aggressive Mode PSK Vulnerability Scanner (Bugtraq ID 7423)
Supported Attributes
Ciphers : DES, 3DES, AES-128, CAST
Hashes : MD5, SHA1
Diffie Hellman Groups: DH Groups 1,2 and 5
IKE Proposal for Peer: xx.xx.xx.xx
Aggressive Mode activated ...
Attribute Settings:
Cipher DES
Hash SHA1
Diffie Hellman Group 1
0.000 3: ph1_initiated(00443ee0, 003b4760)
0.016 3: << ph1 (00443ee0, 244)
0.016 3: >> 84
0.016 3: sx_recv_notify: error 14
0.016 3: sx_purge_spi: implement me - 0
2.516 3: << ph1 (00443ee0, 244)
2.516 3: >> 84
2.516 3: sx_recv_notify: error 14
2.516 3: sx_purge_spi: implement me - 0
5.531 3: << ph1 (00443ee0, 244)
16.047 3: >> 84
16.047 3: sx_recv_notify: error 14
16.047 3: sx_purge_spi: implement me - 0
19.547 3: ph1_disposed(00443ee0)
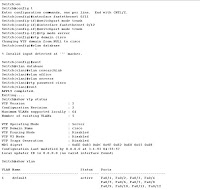
Attribute Settings:
Cipher DES
Hash SHA1
Diffie Hellman Group 2
19.547 3: ph1_initiated(00443ee0, 003b4c08)
19.578 3: << ph1 (00443ee0, 276)
19.578 3: >> 437
19.625 3: ph1_get_psk(00443ee0)
*****************************************************************************
* System is vulnerable!! See http://www.securityfocus/bid/7423/ for details *
*****************************************************************************