Ok, i finally managed to finish my VoIP enumeration experiments and now its time to blog it here. I know it has been long waited, but well, i was rather busy with some other stuffs too. Before i start, i presumed that most of you guys who is reading my blog will have some basic knowledge of how SIP signaling works. There is a plethora of information regarding how SIP signaling works, so just google up and you will find it. The one i visit most is at iptel.org. In this experiment, the tools used are nmap, siVus, sipsak, ser pbx, debian OS, netcat, solarwinds toolset, x-lite softphone and wireshark.
Enumeration is the most important step in all hacking activities. Without a successful enumeration, you wouldn't know if a pbx server is running or what other services is running, so successful enumeration will lead to successful hack. I guess most of you guys know about the three way TCP handshake. Nmap can be used to perform SYN, ACK, Xmas, TCP and other scans. As for VoIP, there is no such options and the best open source tool to use is sipscan or maybe siVus. There are three different scans that can be used to perform a VoIP enumeration and they are the INVITE, OPTIONS and REGISTER request. You guys have to know how handshaking takes place for all three requests. Different scans will yield different result and if the pbx server is harden or patched, then enumeration becomes a little tricker.
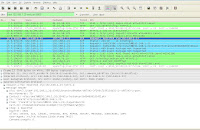
I had managed to setup a SER pbx server without any mysql authentication. This is just for testing purpose only. The Session Initiation Protocol works quite similar to HTTP. With requests you get responses. The requests can be INVITE, REGISTER, OPTIONS, SUBSCRIBE, NOTIFY, REFER, CANCEL, BYE and the response is a number like 100, 180, 200, 303, 408, 500, 603 and many others. For a full list please refer to iptel's website. A successful request will always give a response 200 code, so please take note of that. For the screen shot below, i had successfully sent a INVITE request and you guys can see how the handshaking in wireshark take place.
This tells us that the user does exist in the pbx server, else a 401 or 404 response will be shown. Try this, setup a mysql authentication service and you wont see a 200 response code.
Below shows a screenshot of a REGISTER request. Notice the handshaking is different from the INVITE request.
A REGISTER request allows a user to register its username, password and some other details into the REGISTRAR. So as shown above, the pbx server does allow me to register.
You can use the serctl ul show command to see a list of users as shown below:
I had register two users, Ronald and test.
On the softphone side, if the pbx is setup correctly, all you have to do is launch the softphone and it will automatically register itself to the SER database.(Without authentication for my experiment) The softphone is easily to configure, you will have to enter the correct settings. Below shows a successful registration of the softphone to the pbx server.
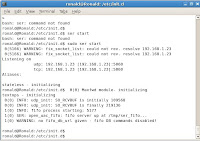
To start the SER service, go to /etc/init.d and type sudo SER start. Once the service is started, you will see some text as shown below:
To check the SER service running in debian, use ps -ef | grep SER as shown below:
To monitor the responses omitted by the pbx server, issue the serctl moni command as shown below:
From the output, you can clearly see the highlighted 2XX response. This shows that there are 2 requests at the moment of testing and both requests are accepted. However, all other responses like 3XX, 4XX, 5XX or 6XX are 0. Which means that there is no bad requests supplied to the pbx server and so the server is not omitting any bad response.
Ok, now comes the enumeration technique. I use netcat to see if i am possible to successful see any response from the server. From the output of netcat, sad to say, there is no response from the server. Its either i type wrongly or the server is configured by default not to show responses. A snippet of netcat is shown below:
siVus was used next to scan the pbx server. The result only displays the port number and the User Agent(UA) which is x-lite softphone. It doesnt show the version or the software of the pbx server.
Sipscan was next. Because there is no authentication setup in the pbx server, all the responses from sipscan gived a 200 response. This means that if an attacker knows the ip of my pbx server, all he needs is just use a softphone and he can register without any password and start using the VoIP service. Of course, in the real world scenario, most pbx server is setup with passwords. My point here is, because my pbx server is setup without any authentication, that is why all the you see a 200 OK response. However, if a pbx server is setup with password, based on the different scan requests with INVITE, REGISTER and OPTIONS, you will see a 4XX response from the pbx server. This will allow you to enumerate user accounts. So after multiple tries and if you see a response like 401, you know that a user exist in the database and it requires authentication. Well, that is good enough having the username of the user. You had successfully enumerated a user in the database. This is a long process. However, you can always write a script to automate this process or you can choose to use sipscan which comes with a default userlist. You will have to update this list to perform a dictionary scan. Below is a snippet of sipscan:
Sipsak is known as the "swiss army knife " which blends well with SER and x-lite softphone. The options i use for sipsak is as below:
Send an OPTIONS request to test@192.168.1.23 and display received replies.
sipsak -vv -s sip:test@192.168.1.23
Trace the SIP path to test@192.168.1.23
sipsak -T -s sip:test@192.168.1.23
Insert a forwarding contact for myself at work to me at home for one hour and authenticated with password if required.
sipsak -U -C sip:WW@home -x 3600 -a password -s sip:WW@192.168.1.23
A usrloc test with additional invites send to the user.
sipsak -U -I -s sip:test@192.168.1.23 -vv
Send the instant message "Hell time!" to the colleague and show result:
sipsak -M -v -s sip:test@192.168.1.23 -B "Hell time!"
To update your hacking toolset you can visit this page: http://www.forinsect.de/pentest/pentest-tools.html
Of course, you can perform more VoIP hacks. The enumeration technique is just one part of it. Too see more VoIP hacking tools and its purpose, check this site out:
http://www.voipsa.org/Resources/tools.php. It has a whole suite of tools for VoIP. Each section has different specific use.
A point to note, please disable any SNMP services in any VoIP devices. Set a strong unguessable public and private SNMP community string if you need to use SNMP, or better still, use SNMP version 3 which provides strong authentication. Below is a snippet of solarwinds. You can use solarwinds to search for the MID and the OID for a specific vendor. Once the vendor is found, a wealth of information will be disclosed. This all happens if you use the default public community string, so keep that in mind.
Lastly, do you know that hardware VoIP phones download configuration setting file from TFTP servers to their firmware upon starting up. Most of us knows that TFTP server runs on UDP port 69 and provides no authentication. So what if you can compromise the TFTP server? You can then actually place rogue files in the servers to corrupt the hardware phones. Well, if you ask me how to check for the TFTP server IP address, you can always check it with your phone settings and normally one of the option will show you the TFTP server IP address. The Cisco IP phone 7940 and 7960 actually does show it. See my previous post. The best way to protect anyone from accessing the TFTP server is to use access-list to permit only certain IPs that can use the TFTP server. Well, there is more than just enumeration and this is just the beginning of VoIP hacking or you can call it phreaking. Once a successful username is found, you can perform MiTM sniffing to capture voice calls and also if you see my previous post, you can actually perform a rerouting of calls. This is all for now. I hope you guys like it. Let me know what you guys think?
Jumat, 30 Maret 2007
VoIP Enumeration Technique released
08.06
No comments
Langganan:
Posting Komentar (Atom)























0 komentar:
Posting Komentar